
To start, we're going to look at some background information which will give you context when you're working on your site and help you to make informed decisions.
How do Joomla Sites Get Hacked?
A common idea among website owners is that because they are not a "big deal," it's unlikely they will be targeted for attacks. It's similar to how many American small businesses view the IRS – "I'm not big enough to audit."
There are a couple problems with this idea:
- It assumes that it takes work for a hacker to attack your site. In reality, most attacks are automated and based off of known Joomla vulnerabilities. The same way that the CEO of Google is not collecting sites for its results, hackers have roving programs looking for vulnerable sites on the web.
- It assumes that your site has no value to hackers. Every website has value to a hacker.
Why Your Joomla Website is Worth Hacking
A hacker can use any website to do a number of valuable things:
- Send spam email.
- Collect private information from your customers or clients.
- Boosts the search engine rankings of other websites by embedding links to them on your website.
- Route traffic from Google from your site to other sites.
- Embed files that alter the analytics of other websites in order to make it seem as if SEO or other marketing is working when it is not (fake results for another business and enterprise.)
- Deliver malware to compromise visitor computers (Think of this like a combination punch. First they attack you, then they attack your visitors.)
- Encrypt and ransom your files back to you (newer.)
What Changes After You've Been Hacked
Initially, not much may change after you've been successfully hacked. Some scripts will just install a shell for a hacker to later use at their convenience.
What's a shell? A shell is one of the things that is commonly added to a hacked site. It's a utility script that analyzes your Web server environment for other vulnerabilities and makes it easy for a hacker to make changes to your system. It enables them to upload files, change permissions, and access your database. It's like a hacker toolbox.
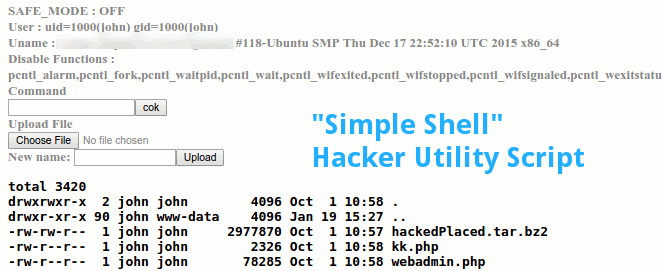
However, a shell is a script that may or may not be there. The reason to use such a script is because of what a hacker will place on a compromised Joomla site.
There are three main areas that will be changed once you've been hacked (though each case is different and you don't have to have changes in all three):
- Malware added. Malware is commonly referred to as viruses, worms, or trojans. This is mostly desktop software that will be delivered to your visitors computers when they load your site in their browsers. This is the results of the combination punch I mentioned above. Malware is constantly evolving and can look like almost anything – normal files and even images.
- Files changed or added. When a hacker is successful in compromising your Joomla site, they will alter your file system to initiate a number of bad things as outlined above.
- Database entries added or changed. Oftentimes, a successful attack won't impact your file system significantly, but your database will be changed. In this kind of attack, the normal operation of your Joomla site will include the changes in your database in order to cause damage. For example, your Joomla articles might have JavaScript injected into them that causes the page to change to another site when that article is loaded.
For any of these areas, you can be sure that whatever changes happen, they won't be obvious. Hackers are in a constant arms race with security professionals. It's like the Mad cartoon Spy versus Spy, where they are continually figuring out ways to trick each other. Unfortunately, this makes the job of identifying hacked files and database entries challenging even when you use good tools.
Because attacks are not always obvious, in Section 2, Is My Joomla Site Hacked?, we'll explore how to to tell if your Joomla site has been hacked. (If you're certain that you've already been hacked, you might want to skip ahead to Section 3: How to Find Hacked Joomla Files.)

