Authors note: the next two sections are the most technical sections of the guide. The techniques are more challenging and I've attempted to provide information about tools that you can use and how to access them, however, as I mentioned in the introduction, you will need some technical skill in order to execute these tasks. I assume that you can do basic technical tasks like use sFTP. Additionally, you will be working on potentially harmful files. Because of this, it's critical that you have anti-malware software installed on your workstation and/or have a secure environment to assess the files in like a "sandbox" virtual machine. Do not run or execute any suspected malware (E.g. oddly named binaries or programs, opening an image you don't recognize in an image viewer, and etc.) Finally, because you will be removing and editing files, always start with a backup!
In this section, we'll explore how to identify hacked Joomla files and database entries so that you can remove them (These approaches don't change whether you're trying to secure a Joomla 1.5, Joomla 2.5, or Joomla 3 website.)
What Does a Hacked Joomla File Look Like?
 Classic example of a hacked Joomla file. Obfuscating functions, compression, eval, modified template... This is another shell script.
Classic example of a hacked Joomla file. Obfuscating functions, compression, eval, modified template... This is another shell script.
The most common sign of a hacked file is obfuscated code. Essentially, anything that looks like a long line of gibberish is likely an injected attack. Especially if it's next to an obfuscating function like base64_decode. Real code may be Greek to the layperson, but it still doesn't look like a machine wrote it.
Hacked files also tend to have very poorly written code with loose organization where functions are enormous and variables crammed together.
It's common for hacked files to reference other websites or to use specific functions. See further down on the page for a list of common functions in hacked files. Please note that the existence of such a function does not mean that a file has been hacked, just that it adds to the evidence that it may have been.
Another sign is any reference to an off-site URL or an oddly named file. E.g. include('../../templates/beez_20/b996.php'). Similarly, a reference to a normal sounding file in an odd location is another indicator of an attack. E.g. include('../../templates/beez_20/settings.php').
Likely Targets for an Attack
Because of how Joomla works, it's common for attacks to focus on files that are always loaded when the application runs. The three most likely affected files are:
- Joomla's index.php
- The template's index.php
- The site's htaccess
Attacks on these files are very obvious and more devious hacker scripts dig deeper into the system when they make their changes. For example, targets include files in system and content plug-ins, language files, and core templates.
Verifying a File is Hacked
To know for certain whether or not it is hacked code, download an unaltered file from the extension or core matching the version you are checking and create an MD5 checksum on that file and check it versus the MD5 checksum on the one that you believe is altered. This acts like a fingerprint and will tell you unequivocally whether the file has changed versus the version that it is supposed to be.
Here are tutorials on how to generate a MD5 checksum:
- Using MD5SUM to Validate the Integrity of (Downloaded) Files (Linux/Windows)
- Generate & Compare MD5, SHA1 Hashes For Files In Terminal (Mac)
More information about MD5 checksums from the official Joomla documentation: How to determine a package checksum
Locating Hacked Joomla Files
In looking for hacked files, there are two things to keep in mind:
- Hacked files and database entries are altered in some way.
- Hackers add files to create vulnerabilities or provide another kind of exploit.
- Hackers seek to achieve some goal by doing this.
These may seem glaringly obvious, but they are going to help us to narrow in on what has been hacked instead of just throwing tools at the problem and hoping to hit on a solution.
If we know that hacked files and database entries are altered in some way how can we tell what has been changed? Two ways:
- We can compare versus an old backup.
- We can create a copy of our site from the same versions of the software installed on the site and compare it for changes.
Comparing Files
 Comparing with Meld
Comparing with Meld
Here are a couple tools you can use to compare files:
- Diff (Linux/Mac)
- Diff Tools on Mac
- Meld (Linux/Windows)
Finding Hacked Joomla Files with a Backup
The first approach is the easiest. However, you have to actually have a backup that you can restore somewhere and you have to be able to have confidence that that backup was an altered. Because you don't know exactly when you are hacked, you have to go back in time far enough to where you can be reasonably sure that you were not hacked then. If your site doesn't change much, and you have backups that are several months old, I would go back two months, if possible.
Some people rely on their web host to manage backups for the site. In this case, often times, the host will delete backups after a certain amount of time. If you're lucky, they will maintain certain time period snapshots and you'll be able to get a snapshot at 45 days or three months. Ideally, they will restore the backup into a subdirectory for you to access. However, each host is different and you will have to contact your web host if you have been relying solely on them for backups.
To compare the backup versus the current version, download both file structures into side-by-side directories. Then, use a difference scanning tool to compare the two file directories. Once this is completed, save both databases as a SQL dumps and run the same difference scanning tool to look for anomalies.
This approach takes a few hours, but it will show you exactly what is been changed and what to remove and fix. Note that if your Joomla site was updated between the backup in the current version you will have several false positives.
The weakness of this approach is that because you don't know exactly when your site was hacked, potentially the backup you restore has been compromised as well. Additionally, you need backups to even try this.
Finding Hacked Joomla Files with a Clean Comparison
This approach doesn't require a backup, but works very similar to the first approach.
- In your Joomla extension manager, under the "manage" menu link, you simply compile a list of all your Joomla extensions and their versions installed on your hacked site.
- In your template manager, you do the same.
- Download a copy of Joomla that is the same version as your hacked version, install it, and install all the extensions and templates at those same versions (you don't need to configure anything.)
- Place your Joomla site in a directory next to your hacked site and run your file compare tool.
This is very similar to comparing to an old backup, but you can be confident that you're comparing against clean files. However, the weakness of this approach is that it doesn't identify any attacks on your database and it takes 4 to 5 times longer to do rather than comparing against a backup. If you have lots of extensions installed, it can take you up to a day of work just to create a matching clean version of the site. Finally, you should note that if you have had any custom work done it will show up in your file compare tool.
Finding Hacked Files with Pattern Matching
If we know that hackers seek to achieve some goal by altering database records or Joomla files, we can look for changes will that would effect those goals.
Think back to the symptoms list from the section, "Is my Joomla Website Hacked?" Any file, function, or other code that could generate the symptoms means that we should look more closely at these areas. These are side effects of hackers achieving their goals and they all revolve around a particular set of needs that hackers have in order to effectively use your site. It's like planning a trip to a distant city- there are only so many roads that get there.
This is important because we can use tools that detect patterns in the code which may indicate a file or database entry has been compromised. For example, here are a few common "roads" that a hacker altered file may have to use to get where they want to go:
- base64_decode
- eval
- exec
- strrev
- wget
- file_get_contents
- stream
- create_function
- assert
- system
- preg_replace
- gzuncompress
- gzinflate
- str_rot13
- curl_exec
- header
- location.href
- encodeuri
- encodeuricomponent
- any link or domain
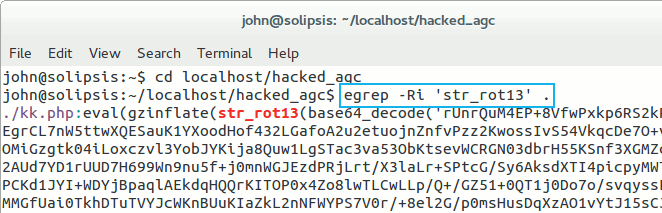
Using tools, we can scan for matching patterns for these strings. The most basic to use is grep or egrep. If you work in Linux, like I do, this is available by default. It's also on Mac. However, if you run Windows you may need to download a comparable tool like PowerGREP.
For any search on your file system, you'll want to be case insensitive. To scan your database, export it using PHPmyAdmin or another MySQL client into a text SQL dump. Then you can run the same searches on it.
A basic grep search looks like:
egrep -Ri 'location.href' mysitedirectory/
Here is a tutorial with more indepth explanations on how to get a grep on finding patterns: Linux and Unix grep command
The strength of using patterns to locate hacked files is that it's very quick and doesn't require setting up a backup or a comparable site. The weakness of pattern matching is that you can miss things. Hackers constantly look for ways to avoid these sort of file scans seeking trickier and trickier ways to achieve their goals.
Finding Hacked Files Using JAMSS
JAMMS is an excellent script developed and maintained by Bernard Toplak. It stands for Joomla! Anti-Malware Scan Script.
It is another tool that uses pattern matching to identify files that may be hacked. Similar to other file scanning tools, it will return many false positives, so you need to be careful and check to make sure that any changes or removals you make based on its results are because the file has actually been hacked. You can use MD5 Checksums as explained above or compare file contents to a clean version.
Using it is very easy, you simply uploaded into your web root, and visit the URL http://yoursite.com/jamss.php
More information and a link to download is available on the Joomla security forum here: http://forum.joomla.org/viewtopic.php?f=714&t=778692
Once you are finished using it make sure and remove it from your site directory!
Finding Hacked Files Using Joomla Extensions
Several Joomla extensions available will do the pattern matching for you in their file scanner. You can install these on a hacked site and attempt to use them to find suspicious files.
Here are a list of a few of these tools:
The benefit to using one of them is that they're are easy to get set up and scanning. The drawback is that you don't know what they're looking for and what they are missing. The problem is that if you have even one hacked file that you don't find on your site that can potentially reinfect it with even more hacked files after you think you are secure. However, even with that, it's still worth using one just to have an alternate approach to analyzing your files.
Finding Hacked Files Using a Debugger

The most thorough way to determine what is happening in your site is to go through it line by line using a debugger. We use PHP Storm and Xdebug when we're doing our debugging. I'm not going to the details of how to do this, because it is going beyond the target reader of this guide. If you are developer and you can't identify where the attack is being pulled into your site's code, this approach will tell you exactly where's it is occurring and what it is doing. The downside to this approach is that it can only detect hacked code that is being loaded. If you are unaware of a successful attack on your site that is not entering through your main index.php file, this will not detect it. With that caveat, it's quick and effective.
What Do You Do If You Can't Find What's Hacked?
Hackers are tricky and if they've compromised your site, they're already in a better position than you are. This is because the average Joomla site has thousands of files to hide their attack in. It's like trying to find a single tree in an entire forest. So what you do if you just can't figure it out?
You have a couple options:
- You can hire someone else.
- You can create a 100% clean version of your site.
- You can create a 90% clean version with a new Joomla install and old database.
Hire Someone to Clean it
For paid cleanup, a cost-effective service for many Joomla users is Sucuri. They also offer ongoing protection and have an excellent reputation. However, you'll still need to do some work to patch the vulnerabilities and improve Joomla's security if you use Sucuri. The section on How to Secure Joomla is helpful for this.
Full disclosure: we are a Sucuri referral partner. We are a referrer because we've used them for monitoring sites and have been impressed with their service and software.
Create a 100% Clean Version of Your Site
The point of doing all this work is not so that you can no how you were compromised or what files were affected. The point is to get back on your feet. So, if you absolutely cannot figure out what is going on, you can still get to a secure position by simply rebuilding your site with clean files. This is incredibly labor-intensive because you have to rebuild everything piece by piece, but you can be sure that everything that you don't transfer over directly is clean.
You still need to be careful because you will need to bring in items from the old site to the new site. For example, you'll likely want to copy over images, articles, and your template. You'll want to go over any of this with a fine toothed comb before copying it into your brand-new site. Once you have your new site set up, you'll also want to make sure everything is up to the current version (see "Secure Your Joomla Site To Keep from Being Hacked Again".)
Create a 90% Clean Version
Remember: do not attempt this on your production site, but in a staging environment first and with a backup!
- In a development environment, setup a copy of your hacked site.
- In a separate directory, download and install Joomla at the same version as your hacked site.
- Install clean versions of your extensions in the new version of Joomla.
- Install your template from the provider if you purchased the template. If the template is custom developed, you'll have to examine it by hand to make sure that none of its files have been hacked before copying it over.
- In your new site, change the configuration.php file to point to the hacked site database (see below for more information.)
- Now your new site should be exactly like your old site, except with a clean file system.
- Update your Joomla! core and all your extensions to their latest version.
- Follow the instructions to Secure Your Joomla Site To Keep from Being Hacked Again
- Delete all the files from your live hacked website and replace it with your new clean version. Important!!! You cannot simply overwrite your old site because most hacker scripts will litter your file system with additional files and backdoors. Everything must be removed before you update your server with your new, clean, site.
What variables to change in the configuration.php file to point to your old site's database:
In the new site you have built, at the root level, is a file named configuration.php
You want to change your database credentials to the old hacked site database. There are three variables that you change to do this:
public $db = 'change_to_your_old_db;
public $user = 'change_to_your_old_db_user';
public $password = 'change_to_your_old_db_password';
You change the values encapsulated in the single quotes to connect to the old database where all your data resides (old username, password, and database)
Once you've done that, you have essentially a clean new body (the files) and an old brain (the database).
This will eliminate most problems on most hacked sites. However, if your database has been compromised, this will do nothing to address it because only the file system is changing.
In the next section, we will cover how to scan for malware in your file system.
Section 4: How to Scan for Malware On Your Joomla Site

