A hacked Joomla site is like a rowboat with holes in the bottom. You need to get the water out to stay afloat and you have to plug those holes or you're constantly going to be bailing water. The previous two sections have focused on getting the water out of the boat and eliminating the damage caused. This section is much easier, but just as important. This is where you plug the holes.
Most successful attacks are caused by software being out of date. Sometimes it's the Joomla core that you let fall out of date and sometimes it's the extensions you use. The remedy is simple: update everything to the most current version. This is simple, but time consuming.
To start, you need a staging or development environment to work in. This is because it's common for extension updates to break certain parts of your site (Joomla always updates gracefully, but extensions are of varying quality version to version.)
Make a List of Extensions to be Updated
Once you have a staging environment set up:
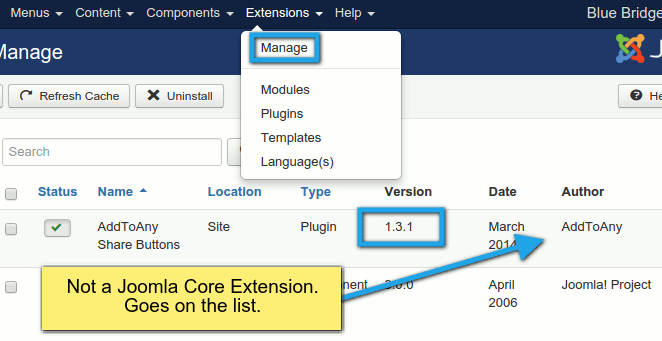
- Open up notepad or a similar document editor to take notes.
- In your Joomla extension manager, under the "manage" menu link, compile a list of your Joomla extensions, their authors, and versions in Notepad. You can ignore "Joomla! Project" extensions.
- If you think you're not using an extension, mark it for deletion. You don't want anything on your site that is not in use. Code that doesn't exist cannot be hacked.
- At the bottom of your administrator control panel, note the Joomla version and add it to notepad.
Once You Have Your List of Updates
- Go through and delete all extensions you don't believe you need.
- Test your site to make sure everything still works as you need it to. This is to catch any problems where you are actually using something you didn't think you were.
- Update your Joomla core by downloading and installing a patch in the extension manager or by using the built-in update functionality.
For each remaining extension on your list:
- Check the provider for an update. In particular, you want to look for security patches in their release log.
- Check the Joomla Vulnerable Extension listings to make sure the extension and version aren't listed.
- Download and update each extension to the latest version. Once you've done so, strike it out on your notepad list.
- Once you have updated everything, test your site again for overall function.
If things are working, all you need to do now is wipe out the old site from the Web server and install your new site in its place (Once again, a reminder: backup, backup, backup.)
Should You Update Your Joomla Core to the next Long-Term Support Version?
Short answer: yes. Typically, this requires more work, and if you cannot justify the cost, most major versions of Joomla at end-of-life are very secure. However, in late 2015 a serious vulnerability was discovered that affected all versions of Joomla and requires a patch on top of being at the last minor version. Additionally, just because the Joomla core is tough to hack at those versions doesn't mean the extensions it uses are. As time passes, it's more and more likely that vulnerabilities will be discovered in out-of-date extensions.
Okay, Joomla Is Up-To-Date, Now What?
There are a few additional tasks you should do. These are below.
However, for an in-depth guide on bullet proofing joomla, checkout our Joomla security checklist.
- Update your passwords, including your hosting, SSH, and FTP passwords.
- Check your users to make sure that no one is a super admin or administrator who shouldn't be. A common attack result is that a normal user has their permissions escalated to that of a super user.
- Check your access levels to make sure that they are correct and set to the default levels that ship with Joomla. Similar to users getting their permissions escalated, you don't want your access levels changed where registered users can install software.
- Check your version of PHP to make sure that it is a secure version (at the time of this writing, it should be 5.5 or newer.)
- Disable anonymous FTP if it is enabled on your server (it shouldn't be, but you can check with your host.)
- Update your file permissions to make sure your directories and files have the correct permissions set and cannot be altered directly.
- Install and configure security software. In particular, a web application firewall can be effective in preventing your defenses from being probed repeatedly with hacker scripts. Below is a list of extensions you can install that will do this.
- Set up automated backups if you have not already. Having backups available is essential in recovering from all kinds of disasters including being hacked.
Joomla Firewalls
In the next section, we will look at how to get your site off of a blacklist.
Section 6: How to Get Your Site off of Blacklists

